 [ad_1]
[ad_1]
Ransomware is one of the most disturbing types of malware that have emerged in recent years. It works by limiting access to computer files until payment of a ransom. The victims included the British National Health Service, the Spanish telephone company Telefonica, the Russian oil giant Rosneft and many others.
Victims are usually required to pay a ransom of Bitcoins equivalent to a few hundred dollars to release their files. Typically, the ransom increases over time until it expires when the files are presumably destroyed. Many companies and individuals have had little choice but to pay.
And this raises an interesting question. How much money did the Bitcoin ransomware programs generate for their malicious masters?
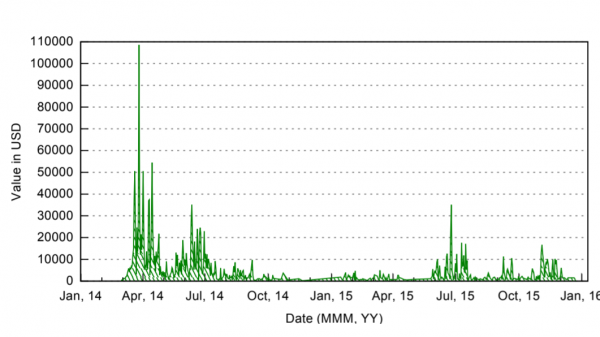
Value in US dollars of redemptions paid to Bitcoin accounts of CryptoWall
Today we receive an answer thanks to the work of Mauro Conti at the University of Padua in Italy and a couple of colleagues. These guys have created a database of Bitcoin accounts used by criminals ransomware and have added up the ransoms paid to them. The result is a complete analysis of the gains made by cybercriminals in this emerging area of crime.
While ransomware can request payment in kind, Conti and Co focus only on those requesting Bitcoin payments. This is because Bitcoin transactions are openly registered and are free to be viewed. So, in principle, it should be possible to calculate exactly how much each account receives. "Our goal was to accurately measure the dollar value of these payments," says Conti and co.
The team began by creating a Bitcoin account database associated with this type of activity since 2013, when the Cryptolocker ransomware became the first to request payment in Bitcoin. "We found twenty ransomware that met our selection criteria, ie those ransomware: (i) that used Bitcoin as at least one payment method of the ransom and (ii) for which at least one Bitcoin address is publicly known," they explain.
For each species of malware, they provide a useful overview of how it works and spreads and how it has evolved over time.
Not all payments for these accounts are necessarily redeemable. Thus Conti and co have developed a way to distinguish ransom payments from other types. They do this by looking for the payments that correspond to the specific amounts that malware requires in ransom.
Finally, Conti and co add up all the redemption payments received from each type of malware. Their work reveals the most lucrative ransomware, but it also raises questions about how these accounts are used and how they can be monitored.
By far the most profitable form of ransomware turns out to be CryptoWall, which started to infect Windows computers in November 2013. It encrypted files using the RSA-2048 encryption algorithm and then requested a payment of up to $ 1,400. to release them.
The malware spreads through various carriers, such as download links sent by the Cutwail spam botnet. Some versions of the malware have created a unique Bitcoin payment address for each infected user and have used the Darknet Tor system to provide anonymous links to each victim.
Between its publication and December 2015, Bitcoin addresses associated with this malware received $ 2.2 million in Bitcoin payments and an additional $ 2.3 million in high value transactions, which Conti and co suspect could also be ransom payments.
Curiously, the total value of the payments received from these Bitcoin addresses was over 45 million dollars. Most of these transactions were not directly linked by Conti and Co to redeem amounts. This is a significant amount of money and raises the obvious question about what the payment was.
The complete ranking of Bitcoin ransomware projects for the amount in US dollars that they generated is as follows:
Ransomware Bitcoin redemption received a USD value
CryptoWall 5.351.2329 2.220.909,12
CryptoLocker 1403.7548 449,274.97
DMA Locker 339.4591 178.162.77
WannaCry 47.1743 86.076,76
CryptoDefense 126.6960 63.859,49
NotPetya 4.0576 9.835.86
KeRanger 9.9990 4.173.12
Interestingly, the WannaCry epidemic has received tremendous media coverage from the spread of malware. But the attack was thwarted by computer security researcher Marcus Hutchins, who discovered and activated a built-in kill switch that prevented malware from being more destructive.
"The overall impact (including financial losses) due to WannaCry's infection could have worsened … thanks to the early detection of the kill switch, which prevented infected computers from further spreading WannaCry," say Conti and co.
The team also discusses other forms of malware that they have requested but do not seem to have received any substantial redemption. These include TeslaCrypt, Hi Buddy! And KillDisk.
Several other groups have conducted similar analyzes and come to similar conclusions. However, Conte and co make their data sets publicly available so that others can build it. "The dataset contains a detailed transaction history of all the addresses we have identified for each ransomware," they say.
Cybercriminals use Bitcoin because it provides a seemingly anonymous way to collect and make payments. However, Bitcoin is pseudonym rather than anonymous. This means that users can protect their identity as long as none of their transactions can be linked to their true identity. But as soon as a single transaction is linked to personally identifiable information, all their transactions become linked in the same way.
A useful analogy is for authors who publish under a pseudonym. As long as the identity of the author is never connected to any of the pseudonymous articles, he or she remains anonymous. But if it is connected to a single pseudonym article, it is connected to all of them, and therefore anonymity is lost.
So pseudonym protection is a fragile thing. A single transaction linking a Bitcoin account to a personal account can reveal the identity of a cybercriminal. And personal data is continually lost in web-based transactions.
We wrote about the imperfections in the anonymity of Bitcoin transactions last year. This should provide some hope of tracking down these criminals.
Accounts and co have set this type of investigation as a future goal. "We will try to trace how the ransoms received were used and by whom," they say.
He is brave and ambitious. But it also raises a question: what are the forces of order doing in the meantime?
Ref: arxiv.org/abs/1804.01341: On the economic relevance of ransomware campaigns: a perspective on transactions with Bitcoin