 [ad_1]
[ad_1]
The digital economy is flourishing thanks in large part to the concepts presented in the Bitcoin white paper by Satoshi Nakamoto. This white paper introduced the concept of decentralized cryptocurrency on the market and ushered in the digitization of the global economy. Because of this, many people claim that the Bitcoin whitepaper legitimately earns the title of a historical document .
This single document initiated a 10-year digital transformation of the traditional financial system, providing the world with a viable alternative to current models in practice. Let's take a moment to examine this whitepaper that changes the game.

The Abstract
The first section of the Bitcoin whitepaper is a summary of BTC's purpose, including how it alleviates the need for third-party financial institutions. This introduction to the concept of Bitcoin is also the most cited section of the white paper. Here, Satoshi states in reference to Bitcoin:
"A purely peer-to-peer version of e-money would allow you to send online payments directly from one party to another without going through a financial institution."
Satoshi then briefly explains how a work-based test system based on hash works. Includes a description of how the longest chain is considered the valid chain. The valid chain is the chain on which the network will continue to add transaction data during the mining process. Satoshi also mentions the dependence of the blockchain from honest nodes. 51% of the total hash power of the network must remain honest for the BTC network to remain secure.
The Introduction
In this section, Satoshi explains the problems with the current economic model based on trust. Specifically, it mentions the inability to execute irreversible transactions, even if many services rendered are irreversible. This irreversibility creates the need for more third-party protections that increase transaction costs. Satoshi has seen this loophole in the current economic state as a way for central bankers to continue to control the fate of the economy indefinitely.
After pointing out the errors in the current model, Satoshi explains how a hash-based algorithm could remove the need for trust in the system and replace it with a mathematical equation. This cryptographic equation could be used to verify the validity of virtual currency transactions. Satoshi mentions again the importance of maintaining at least fifty one percent of hashing power to centralize to ensure network security
Transactions
The transaction section of Satoshi's whitepaper explains the problems associated with double spending . He explains how the current method of double spending reduction requires a centralized bank or mint to maintain and review all transactions and ensure that funds are available. This system depends exclusively on the trust of the third party.
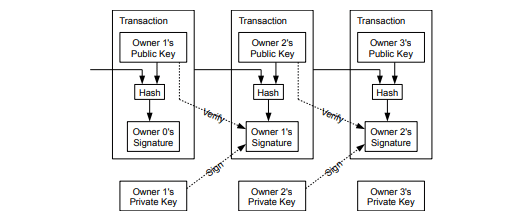
Bitcoin whitepaper transaction protocol schema
In this scenario, it is the banks that manage records and validate transactions. In Satoshi's vision, the scenario is reversed. All transactions are verified through a public accounting using a hash-based job testing system. This system provides the BTC financial structure with greater transparency by creating an open ledger where all blockchain users can verify a transaction through the mining process.
Timestamp Server
Satoshi proposes the use of a server with date and time to capture a record of transaction hashes and then publish them. The timestamp provides concrete evidence that the data existed at that time. Each timestamp contains the data from the previous timestamp. A distributed master book known as blockchain is the place where timestamp blocks are published.
Proof-of-Work
Satoshi cites Adam Back's first cryptocurrency attempt, Hashcash, when he introduces the proof-of-work section of the Bitcoin whitepaper. The labor proof system involves a mathematical equation. The nodes compete with one another to understand the equation, then adding the block after the blockchain. Bitcoin uses the SHA-256 hashing algorithm. The answer to this equation must start with four zeros and requires an intense amount of computing power.
Satoshi explains how the network would maintain its integrity as long as most of the nodes remain honest. As long as fifty-one percent of the nodes do not work together to orchestrate an attack on the network, Bitcoin's blockchain remains safe. Increasing the hashing power increases the difficulty of the network. This increase in difficulty ensures that the blocking time of BTC is approximately 10 minutes.
Bitcoin reward data by Bitcoin Block reward
Network
Bitcoin's network is surprisingly simplistic design. Satoshi has taken this section to track the exact flow of the network. Here are the six steps that lists:
- New transactions are transmitted to all nodes.
- Each node collects new transactions in a block.
- Each node works to find a difficult job test for its block.
- When a node finds a job test, it transmits the block to all the nodes.
- Nodes accept blocking only if all transactions in it are valid and have not already been spent.
- The nodes express their acceptance of the block working to the creation of the next block in the chain using the hash of the block accepted as a previous hash
Nakamoto explains how the BTC network reacts in case of conflict Chains. The nodes consider the longest chain as the valid chain. Transactions are applied to the chain based on their arrival order. If two nodes transmit chains in conflict at the same time, the longest chain is validated. The other chain is saved and if it becomes the longest chain when the next block is added, then it is the valid chain.
Incentive
Nodes receive rewards for being the first to solve the work trial algorithm and add the next block to the blockchain. Originally there were fifty Bitcoins. Today, the mining reward is 12.5 Bitcoins. Nakamoto explains how BTC mining is similar to mining for gold, as resources are spent to conduct both mining activities. In other words, miners pay their efforts to calculate electricity and energy costs.
This system of incentives makes a fifty-one percent attack unhelpful. Satoshi explains that the attacker would benefit the most from continuing to extract my new BTC rather than weakening the system, which, as a result, would undermine their wealth.
Reclaiming Disk Space
Satoshi was well aware that the blockchain could grow to be gigantic. To alleviate future archival problems, he proposed a method in which the old blocks save with most of their discarded transaction data. Satoshi describes how the average PC uses 2 GB of RAM in 2008. Thus, using Moore's law, it estimated an increase of 1.2 GB per year in computing power.
Simplified verification of payments
Satoshi proposes a method in which nodes can verify transactions without confirming the entire history of blockchain transactions. Nodes are allowed to maintain a block header of the longest chain transactions. Again, Satoshi mentions the importance of maintaining the decentralized BTC blockchain. This time describes how an attacker could overwhelm the network for a while if he gets control of fifty-one percent.
Combining and Sharing Value
Bitcoin transactions contain more input and output that allows you to combine or split transactions to reduce blockchain congestion. Most transactions combine inputs from multiple locations. There are only two exits. One is the payment, and the other would be any change from the transaction.
Privacy
Bitcoin is not anonymous. You can track and track Bitcoin transactions using any number of blockchain forensics tools. However, the Satoshi white paper includes a section on how to make BTC anonymous. Here he explains that you could make public keys private. In this way, BTC could operate similarly to the stock market as people could see the size and direction of the transaction but would not be able to determine the sender or recipient.
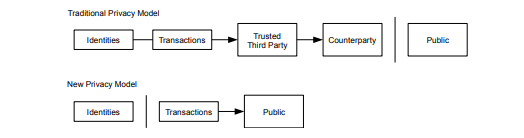
Bitcoin whitepaper privacy scheme
Calculations
The white paper calculations section includes some equations of hacking scenarios. Satoshi claims that the network can be hacked briefly, but those honest nodes would end up returning the network to its full state. He also uses complex equations to show how the manufactured chain would not be able to remain the longest chain, as long as the honest nodes continue to add information to the valid chain.
Conclusion
The conclusion of the Bitcoin white paper focuses on the ability to remove third-party organizations from transactions. Satoshi explains how his system allows a node to come and go as it requires. It ends by describing how to use the consent mechanism to determine any incentive changes or rules in the Bitcoin protocol.
References
Satoshi includes a brief reference section at the end of his white paper. Many of those responsible for his cited works, such as Adam Beck, became important developers in the BTC project.
Satoshi and the Bitcoin Whitepaper
Many would agree that the Bitcoin whitepaper was the first step in digitizing the global economy. Since its entry into the market nine years ago, Bitcoin has managed to become a household name. The cryptomarket is still in the nascent state, but many predict that BTC will remain relevant.
Related
[ad_2]Source link