 [ad_1]
[ad_1]

New research reports from information security companies monitoring online attacks and cybercrime trends show that malicious code developers continue to work hard. In fact, they continue to update or release new versions of cryptocurrency miners, cryptographic ransomware, bank trojans and other malware (see: GandCrab Ransomware: the Cat-and-Mouse game continues).
See also: Key driver to enable digital transformation in financial services
Looking at these efforts from a high-level perspective, they are governed by a simple and direct imperative: "Criminals like to make money," says Brian Honan, who heads BH Consulting in Dublin.
As a result, if a particular type of attack leads to an illegal payday for an individual or group, these attacks are likely to continue. Nonetheless, some gangs seem to continue to diversify using malware droppers – the attack code that initially infects a PC or server – to push a series of ever-evolving attack codes onto victims' PCs and servers.
WebCobra: no joy pack
While ransomware continues to hit organizations, security experts say that what is particularly hot right now is cryptocurrency malware. And a new strain of malicious code called WebCobra, which seems to have been built by Russian developers, is the latest example of malware designed to use the CPUs of infected systems to extract cryptocurrency, say researchers McAfee Kapil Khade and Xiaobing Lin in a blog send.
"Money mining is hard to detect," they say. "Once a machine has been compromised, a malicious app runs automatically in the background with only one sign: performance degradation."
The victims, however, are left to pay the energy costs resulting from all this CPU usage. Crescent Electric Supply Company estimated in January that the cost of extracting a single bitcoin in the United States ranges from $ 531 to $ 26,170, depending on the state in which the extraction occurred.
"The increase in the value of cryptocurrencies has pushed cybercriminals to use malware that steals machine resources to extract cryptographic coins without the consent of victims," say McAfee researchers.
In the case of WebCobra, researchers believe that malware is distributed by shady applications or that the industry often refers to PUPs – potentially unwanted programs – that can be bundled with wallpapers or freely offered versions of paid applications.
Even WebCobra has some ace up its sleeve; customize attacks based on the type of system you can reach. "This cryptocurrency malware is rare because it releases a different miner depending on the configuration of the infected machine," say McAfee researchers.
The coin malware is still hot
Researchers expect the prevalence of these types of attacks to continue to increase, as they have in the last 12 months.
"Coin mining malware will continue to evolve as cybercriminals take advantage of this relatively easy route to steal value," they say. "Mining coins on other people's systems require less investment and risk than ransomware and do not depend on a percentage of victims accepting to send money, and as long as users learn that they are supporting criminal miners, they have a lot to gain."
The ease of execution of these attacks, together with the difficulties that the victims have in detecting them, have led to a considerable increase in these campaigns, security experts say.
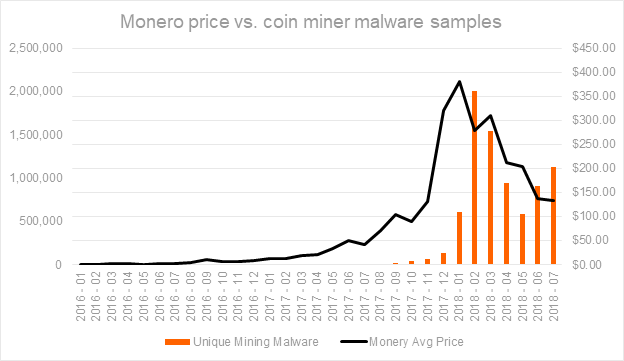
"Surveys of cryptocurrency mines have increased significantly between 2017 and 2018," says the Cyber Threat Alliance in a report published in September (see The cryptocurrency addiction of criminals continues).
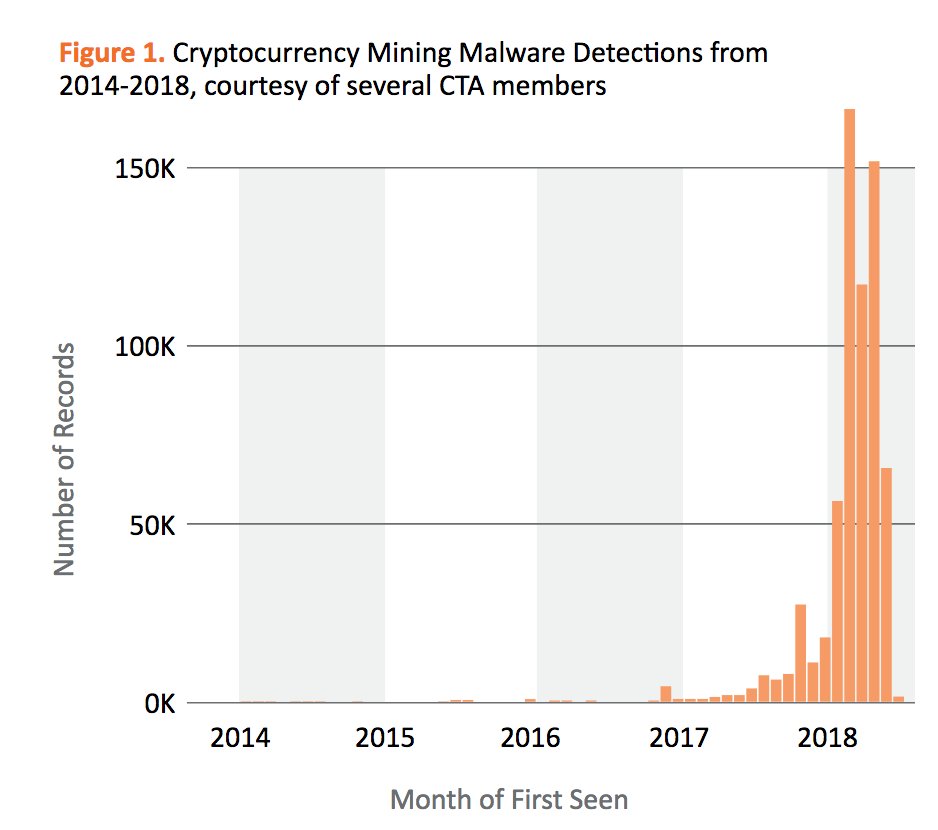
"The combined data from several CTA members show a 459% increase in illegal cryptocurrency malware detections since 2017 and the latest CTA quarterly reports show that this rapid growth shows no signs of slowing," the report said.
Raj Samani, chief scientist at McAfee, says that cryptomining attacks have increased in the last year because such attacks are "simpler, more direct and less risky than traditional cybercrime activities".
Trickbot learns new tricks
Meanwhile, the modular malware called Trickbot, which was also used to extract cryptocurrency, has new tricks.
"TrickBot has traditionally targeted banking customers in multiple geographic areas to steal login credentials in order to commit identity fraud and facilitate fraudulent transactions," Digital Shadows researchers say in a research report.
But TrickBot designers have added additional features that seem designed to extend the reach of malware. In February, TrickBot's designers added an open-source module monero cryptocurrency-mining. And in March they added the ability to encrypt devices, "potentially helping threat actors to extort victims," the research report said.
Last month, Vitali Kremez, director of research at the Flashpoint threat intelligence company, warned that TrickBot was updated to include a module designed to steal passwords from multiple types of applications and browsers.
19.10.2018: #TrickBot #Banker #Malware Group:
New module "pwgrab.dll" or "PasswordGrabber"
Soft targeted ->
{Firefox
Internet Explorer
Microsoft Edge
Google Chrome
perspective
Filezilla
WinSCP}
Dev Comment | Also HTTP ports and odd HTTPS ports
[ad_2]Source link