 [ad_1]
[ad_1]
Nonce is a central part of the mining proof of work (PoW) algorithm for blockchains and cryptocurrencies like Bitcoin. Miners challenge each other find a nonce that produces a hash with a value less than or equal to the one set by the network difficulty. If a miner finds such a nonce, call a nonce of gold, then wins the right to add that block to the blockchain and receive the reward of the block.
Nonce is a random, one-off integer. Miners test and discharge millions of nonce every second. They are hoping to produce a hash value that satisfies the goal and thus win the reward of the block. This is what happens during the PoW extraction at the most basic level, although there is so much more. Here, we will explore the whole purpose of the nonce during the extraction process.
Building Blocks with Nonces
Nonce is a 32-bit number. It remains in the block header along with other key data, such as difficulty level and timestamp. When miners build blocks, they randomly choose a nonce and insert it into the block header, creating a new header block hash.
The hash is a 256-bit number and must start with a huge number of zeros, that is, having an incredibly small value. If he does not have enough zeros, the miner discards the hash and tries a new nonce. This process is repeated until a miner discovers a nonce that produces a hash with a value less than or equal to the one set by the difficulty.
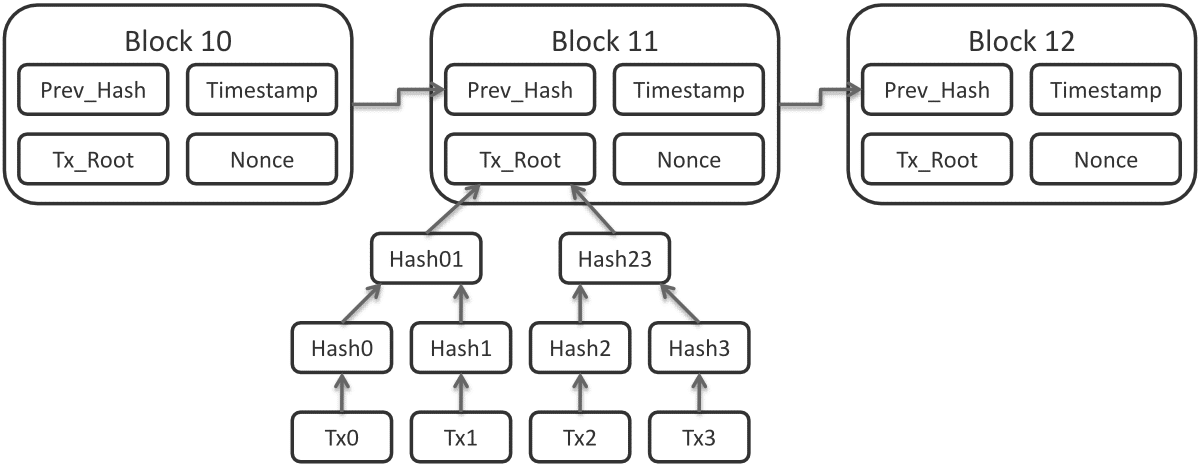
The 32-bit size of the nonce means that there are four billion possible combinations. Although technically, it is much higher because of something called the extra nonce. This is an additional space for a longer nonce, which means you can have tens of billions of combinations.
The nonce is the only parameter that the miner changes, all the others remain static. If the miner finds the gold nonce, he adds that block to the blockchain and receives the reward of the block. Currently, there is no way to speed up the search process for the correct nonce. This means that the miners are only operating in trial and error until they find a nonce of gold. This process is what constitutes the work, in working trial.
Relationship with mining difficulties
As we said, the miner is trying to find a nonce that produces a hash below the value set by the difficulty of the network. The Bitcoin protocol sets this extraction difficulty. As the difficulty increases, the target value of the hash decreases. This means that there must be more zeroes at the beginning of the number of hashes. The probability of finding a lower hash value decreases and therefore the miners have to test more nonce. When a miner blocks a block, the hash must have a value equal to or less than the destination number to succeed.
When Bitcoin is extracted, the difficulty adapts to each block of 2016. This works to be every two weeks. However, other PoW blockchains have faster adjustments. For example, litecoin, due to its shorter blocking time, its difficulty settles every three and a half days. Digibyte, on the other hand, regulates its difficulty with each block in real time.
Because the adjustment is important
If the difficulty does not match, there would be a linear relationship between hashing power and blocking premiums. As more miners join the network and the hashing power increases, there would be a corresponding increase in Bitcoin rewards. This would undermine the controls on inflation on the Bitcoin protocol and with it, its healthy monetary properties.
Fortunately, having a difficulty adjustment, block premiums can be kept relatively stable every two weeks. The difficulty can also adjust lower down though. If the mining profitability disappears, the miners will cease operations and the hash rate will fall. The difficulty will then adapt appropriately. We have seen this now for several months on the Bitcoin network since the difficulty has reached the peak October 4th.
On Bitcoin, after each block of 2016, the Bitcoin client will compare the real time for each block to be generated with respect to the target time. Then he will adjust the difficulty appropriately. The goal is to get miners to produce blocks as close as possible to exactly ten minutes.
Protection through secure Hash algorithms
The resiliency of the SHA-256 algorithm prevents miners from accelerating and deceiving the trial and error process. SHA-256 belongs to the SHA-2 family of safe hash algorithms and was released by the NSA in 2001. If this algorithm was broken, as happened to the encryption class SHA-1 hash algorithms, so the PoW process would be compromised.
There are several ways to break a hash algorithm. By this we mean to be able to circumvent the trial and error method and find the correct nonces much more quickly. Collision attacks they are the most recent and efficient way to do it.
The whole purpose of a secure hash algorithm is to ensure the uniqueness of a hash. When data is submitted to hashes, the inputs must create a totally unique hash number. The only way that the same number can be replicated is with the same identical inputs, including the nonce. A collision attack, however, means that the same hash can be produced by different inputs. An attacker can do it with sufficient computing resources. This completely undermines the purpose of the secure hash algorithm.
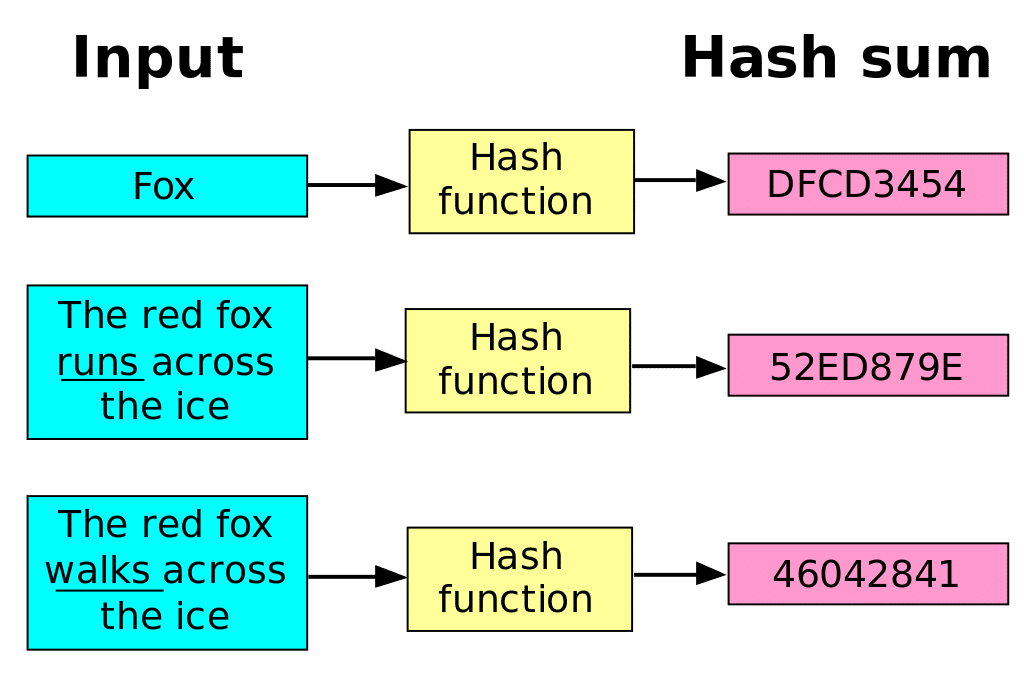
Now that a collision attack has proved to be effective against SHA-1 algorithms, it is no longer possible to rely on it. The attack was made possible in part because of the tremendous progress in computer power over the past decade.
At some point, when computing powers have increased enough, SHA-256 will also be vulnerable to such attacks. However, Bitcoin developers should know it long before this happens. This is due to the fact that such attacks are almost always shown as possible in theory before actually being demonstrated to work in real life. The Bitcoin Core team should therefore rotate towards a newer and tougher algorithm.
It is also worth noting that most Internet authentication protocols currently use SHA-2 algorithms. If they become vulnerable overnight, we would have big global problems well beyond Bitcoin extraction.
Value of the job test
Miners use their hardware to test these problems, with a speed of millions per second. The fact that there is no way to accelerate the search for nonce continues PoW an open and fair system.
The beneficial characteristic of this system is that it requires a great deal of energy, time and capital to resolve the correct value and win the reward. However, at the same time, it is incredibly easy for the other nodes to verify the correct value. This dichotomy keeps the network safe and provides an easy way to reach consensus.
In the end, the nonce is just a small part of the Bitcoin mining process. However, it plays a crucial role in maintaining its integrity. The nonce is the only one and the only thing that a miner changes to find a sufficient hash value. It is really the accelerator, the brake and the clutch for the whole setup.
reported

[ad_2]Source link