 [ad_1]
[ad_1]

An advanced threat group called Bismuth recently used cryptocurrency mining as a way to hide the purpose of their business and to avoid triggering high-priority alerts.
Coin mining is generally considered a non-critical security issue, so the method allowed the actor to establish persistence and move sideways on the compromised network, while monetizing from the attack.
Lure for cryptojacking
Bismuth regularly targets human and civil rights organizations, but his list of victims includes multinational corporations, financial services, educational institutions and government sector entities.
The actor has been running cyber-espionage operations since at least 2012. Since then, his attacks have grown in complexity, combining custom tools with freely available tools.
In recent campaigns, however, Bismuth has launched Monero coin miners on compromised systems belonging to private and government organizations in France and Vietnam.
Microsoft detected the attacks that took place in July and August, saying that the cryptojacking activity did not change the actor’s goal, continuing to monitor and steal information of interest.
“BISMUTH’s use of coin miners was unexpected, but was consistent with the group’s long-standing smelting methods” – Microsoft
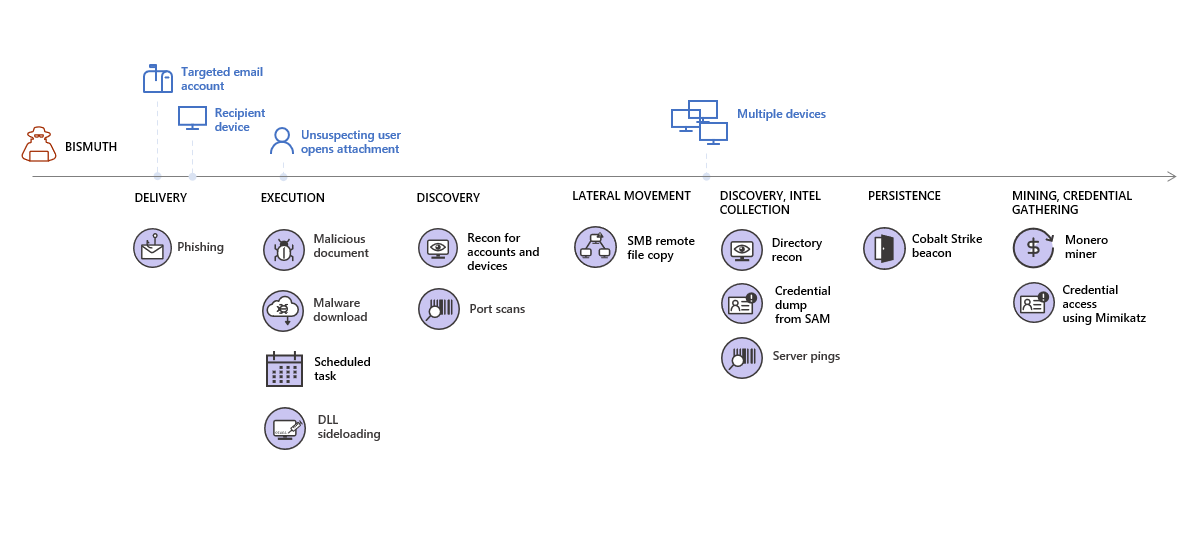
The hackers studied the victims before sending out spear phishing emails created for a specific recipient to gain initial access. Researchers say the attacker also corresponded with the victim to build trust and increase the chances of a successful infection.
Legit and old apps for DLL sideloading
They used Gmail accounts created specifically for each recipient. Microsoft believes that the Bismuth hackers used information from public sources to determine their goals and personalize messages.
Bismuth also used DLL side loading, a widely used technique that takes advantage of the way Windows applications handle these types of files to load a malicious DLL that spoofs a legitimate one.
During the summer attacks, the actor installed previous versions of several applications that were still vulnerable to DLL side-loading. These included Microsoft Defender, the Sysinternals DebugView tool, the McAfee on-demand scanner, and Microsoft Word 2007.
Researchers were able to attribute these attacks to Bismuth based on a custom malware called KerrDown released during the infection chain and used exclusively by Bismuth. The malware represented a Microsoft Word 2007 DLL and ran in the context of the application.
Discovery and dissemination of the network
According to Microsoft, Bismuth spent about a month identifying the computers on the victim’s network before they moved sideways to the servers that allowed them to spread further.
While scanning the network, the hackers gathered details about the domain and local administrators, verified user privileges on local machines, and extracted device information.
Using PowerShell, the actor could fly under the radar and run multiple cmdlets that helped move across the network and perform the attack. The activity involved the following phases:
- steal credentials from the Security Account Manager (SAM) database
- collect domain group and user information
- connect to devices via WMI (Windows Management Instrumentation)
- collect credentials from security logs with event ID 680 (possibly targeting logs related to NTLM fallbacks)
- Collect domain trust information and ping the database and file servers identified during the survey
- install a Cobalt Strike beacon via DLL side loading, using an outdated copy of the McAfee on-demand scanner running with elevated privileges
The installation of the coin miners preceded attempts to steal credentials on local systems (via Mimikatz). While the hackers didn’t make a lot of money from cryptojacking (over $ 1,000 from all attacks), it paid off as it acted as a smokescreen for the actual business.
They also hid this activity by registering them with a legitimate service name. In one case, they used a common virtual machine process.
“Because BISMUTH’s attacks included techniques ranging from typical to more advanced, devices with common threat activity such as phishing and coin mining should be elevated and inspected for advanced threats” – Microsoft
The tactic used by this threat to blend in with normal network activity and the use of common threats that are often ignored as non-critical allow them to perform their operations without the pressure of immediate action against them.
Microsoft says Bismuth shares similarities with a group of nation-states called OceanLotus (APT 32), which are believed to work for the Vietnamese government.
Researchers advise companies not to fend off common threats identified as coin mining and to investigate more advanced hacking activities.