[ad_1]
With Pluton, Microsoft wants to integrate a security chip directly into the processor in the future, thus replacing the TPM. The security processor, first used in 2013 on Xbox One, will also be used on Windows PCs in the future. Microsoft has already found suitable partners in AMD, Intel and Qualcomm.
While the operating system itself may be well protected with cloud protection and advances in AI defense, attacks on hardware-software transitions are now a rapidly growing target, Microsoft explains. This area of a computer cannot be reached with these security measures and cannot be monitored for attacks. Secure core PCs, such as those offered by Microsoft with the Surface series, but also by Dell, Dynabook, HP, Lenovo, and Panasonic, should better protect firmware that uses UEFI.
Pluton in the CPUs of AMD, Intel and Qualcomm
In the next step, Microsoft wants to integrate the Pluton security processor directly into the processors of well-known manufacturers. With AMD, Intel and Qualcomm, Microsoft today unveiled the vision for future generations of Windows PCs. There is still no date when the CPUs of the aforementioned manufacturers will be equipped with Pluton.
According to Mike Nordquist, Director of Strategic Planning and Architecture for Intel’s Business Client Group, it will take more than a year for properly equipped Intel CPUs to hit the market. Hardware changes for Pluton should be as simple as possible and take up little processor space. The addition shouldn’t result in higher CPU costs. AMD says their security processor will continue to exist alongside Microsoft Pluton.
Microsoft is planning a transition phase with TPM emulation
Microsoft is already outlining a transition phase from TPM to Pluton and what activities the chip should take on. Microsoft wants to replace the Trusted Platform Module (TPM) with Pluton. The TPM is currently a separate chip separate from the CPU, which stores the cryptographic keys and is intended to ensure system integrity. In Windows 10, the module is used to encrypt storage media with BitLocker, and the TPM is also used in Windows Hello for logging in via PIN, fingerprint sensor or IR camera. However, new attack methods, particularly through physical access to a computer, attack the channel between the CPU and the TPM to intercept security-relevant data.
The Pluton design is meant to prevent attacks on this channel, since it doesn’t even exist. Windows PCs with Pluton architecture should first emulate a TPM so that the previously used TPM specifications and APIs can still be used, even if no TPM is physically installed. The Pluton processor is supposed to protect login data, user identities, cryptographic keys and personal data. According to Microsoft, none of this data should be extracted via malware or physical access to the computer. The Pluton processor is isolated from the rest of the system and should never expose the keys to other hardware or even its own firmware using the Secure Hardware Cryptography Key (SHACK), which in turn should be protected via the cloud.
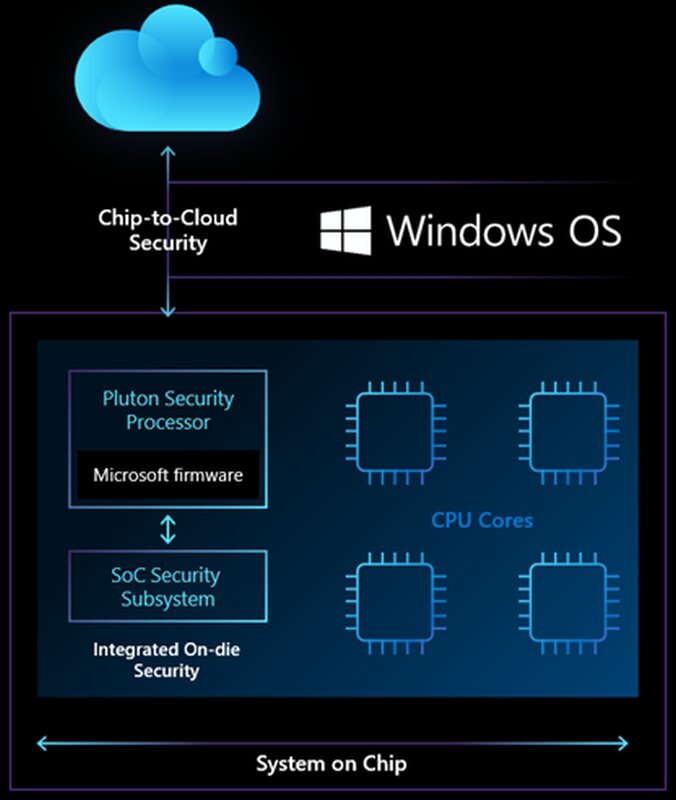
Microsoft talks about chip-to-cloud security with Pluton, since, as with Xbox or Azure Sphere, the integrity of the chip and its firmware from the cloud can be ensured via the Cerberus project published on GitHub. Computers with “Pluton for Windows” should receive firmware updates as well as other updates from a central location via Windows Update. With this, Microsoft wants to close further potential weaknesses, as firmware currently has yet to be obtained from various sources. Microsoft is convinced that processors with integrated security chips like Pluton represent the future of modern hardware.
The security industry is skeptical
A comment from security researcher Mark Ermolov, who discovered security gaps in security mechanisms, especially in Intel processors, shows that not everyone in the industry is necessarily convinced. “Oh no, another “security” processor“It’s his facepalm emoji Comment on the announcement on Twitter. It links to an article by Wired, which also explains that assembling all the security features into a chip can be just as dangerous, as if a gap occurs this element can no longer be trusted. Security chips are by no means foolproof, as both Intel and Apple (T2, Secure Enclave) and Cisco have proven. Talk to David Weston, Microsoft’s Director of Enterprise and Operating System Security Wired so to immediately understand that obviously no protection is ever completely safe.
Oh no, another “security” processor 🤦♂️#Microsoft #Plutohttps://t.co/dxVwd5WhXs
– Mark Ermolov (@_markel___) November 17, 2020
Security chips isolate systems
On the other hand, such security chips are also criticized because they potentially limit the changes a user can make to the hardware or software that can run on the system. Wherever you try to increase the level of security, even the openness of an architecture is potentially affected. Xbox, as a closed system, is a good example of this. In front of Hot Microsoft stated that the installation of other operating systems would not be prevented or interfered with. Additionally, CPU manufacturers may include a shutdown feature for Pluton.
[ad_2]
Source link