
[ad_1]
The Cyber Division of the Federal Bureau of Investigation (FBI) has detected some attacks on US government agencies and US private companies, including in the technology and financial sectors, since April 2020. The target of the attack were instances not configured in a secure of the SonarQube open source platform, designed for automated static code analysis.
Hackers use a known vulnerability in the SonarQube platform that allows operation with a standard configuration: spin on door without modification 9000 and offers administrative access with a username admin and password admin. Mind you, with the software that the associated site advertises under the slogan “Your teammate for code quality and security”, and which is designed to find bugs and vulnerabilities.
Static analysis including the search for weak points
SonarQube performs static code analysis for a total of 27 programming languages. The platform examines the source code for possible errors such as null pointer assignments and security risks such as too short keys or the uncontrolled use of any user input.
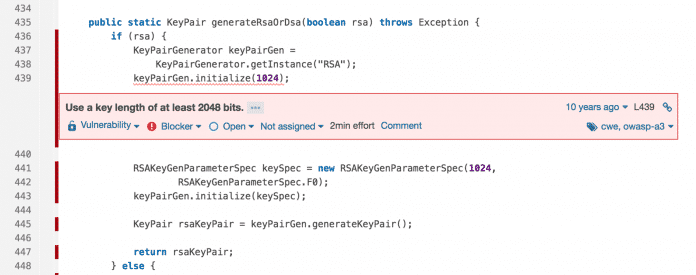
SonarQube helps, among other things, to find inadequate security measures.
(Image: SonarQube)
Source code that enters unsecured SonarQube instances for testing can be accessed using the standard name and password combination.
From April to today
According to its own information, the FBI has detected leaks of source code from instances of SonarQube configured insecurely since April 2020. In August, unknown people reportedly released internal data from two organizations via a public lifecycle archive tool. Previously, in July, corporate data that had been similarly exploited appeared in a privately hosted and publicly accessible repository.
The report suggests a few actions, the first of which should be obvious: Administrators need to change the default settings. In addition, the authority recommends placing SonarQube instances behind a login process and checking whether unauthorized users had access to the platform. Managers should also exchange all available credentials in affected instances. Finally, the FBI recommends placing SonarQube installations behind a firewall.
Since the FBI focuses on the United States, the findings mentioned in the report refer only to them. It can be assumed, however, that European developers and administrators also manage unsecured SonarQube instances.
(rme)
.
[ad_2]
Source link