 [ad_1]
[ad_1]

See also: How to protect endpoints from cybercrime
Anti-malware researchers known as Malware Hunter Team discovered malware, calling itself "Barack's Everlasting Blue Blackmail Virus Obama. " The code was compiled for the first time in May, but was not uploaded to the VirusTotal virus scanning service until last month. The malware includes a number of elements in the Chinese language, even if it is not a smoking gun on who has developed it or on which it is based.
"This is a great thing"
Unusually, the Windows targeting ransomware seems to be designed to encrypt only executable files – .exe -. "Hi, your computer is encrypted by me! Yes, this means that your EXE file is not open! Because I have encrypted it, so you can decode it, but you have to tip it." That's great. "
Obama is not the first world leader to have been celebrated with the "skin" of his ransomware.
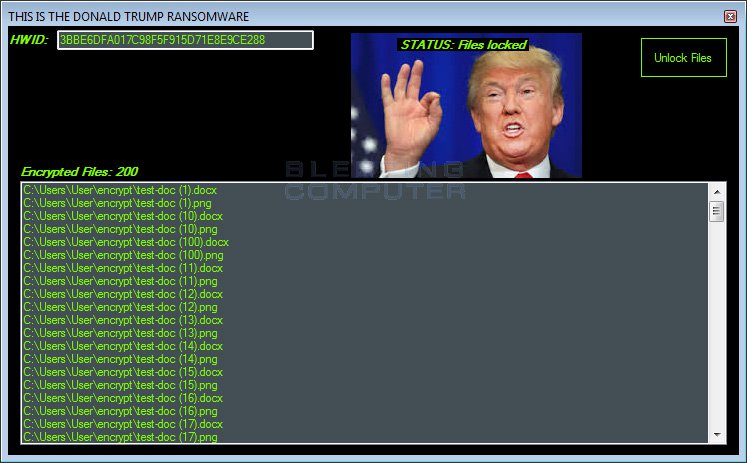
In 2016, Bleeping Computer reported finding a ransomware with a theme by Donald Trump of the then presidential candidate. But the malware version discovered has not been able to encrypt anything and still be under development. It is not clear if a working version has ever debuted.
Cryptojacking continues to rise
The appearance of the Obama-themed ransomware remembers that the cryptographic code may not be as hot as it used to be, but it is still prevalent. Probably, 2017 was the year of ransomware innovation. But 2018 was the year of cryptocurrency malware attacks and "cryptographic" attacks (see Cryptojacking Displaces Ransomware as Top Malware Threat .
Security researchers this year continued to track the rapid increase in malware designed to use the CPUs of the infected systems to extract the cryptocurrency Mining means to solve complex computational challenges that verify the transactions of the cryptocurrency system, which adds them to the cryptocurrency blockchain In return, the miners could receive cryptocurrency as a reward
At the beginning of this year, the security company Vectra reported that from August 2017 to January 2018, "with the increase in the value of cryptocurrencies as bitcoin, ethereum and monero , there was a corresponding increase in the number of computers on university campuses that perform mining or crypted by miners to process cryptocurrency hashes ". It was not clear how much of the mining was malevolent.
But as the value of cryptocurrencies has increased, security companies have tracked an increase in malware attacks on cryptocurrency. Such malware allows attackers to monetize their infections without having to interact with the victims or explain to many how they could acquire the particular flavor of the cryptocurrency that their ransomware attacker requires to use to send their ransom (see Ransomware Gangs Take "Customer Service Approach .)
Cryptojacking Targets Servers
Hackers have also begun to look beyond PCs." Crypto miners are not only installed on workstations, servers are also juicy targets. because that's where the true power of the CPU is available, "says security researcher Xavier Mertens in a post on the SANS Institute's Storm Center website.
" The recent code execution vulnerability remote of Apache Struts … is heavily used to release crypto miners on vulnerable systems, "he adds, referring to the application framework on Apache open source Web Java (see Apache Issues Emergency Struts Patch to Fix Critical Flaw ). [19659000] Monitoring the "Rocke" Campaign
Since April, Cisco's Talos security group claims to have mapped a large-scale cryptocurrency mining campaign that targets Struts 2 and is managed by a Chinese-language hacker . calls "Rocke"
"Rocke actively engages in the distribution and execution of malware in the process of encryption using a varied toolkit that includes Git repositories, HttpFileServers (HFS) and a host of different payloads, including sh Ellos, Backdoor JavaScript, as well as ELF and PE miners, "David Liebenberg, a senior threat analyst for the Cisco Talos Threat Intervention Team, says in a blog post.
In July, Talos detected attacks, related to Rocke, it seems he is probing vulnerable Oracle WebLogic servers.
"Although for the first time we have observed this actor exploiting the vulnerabilities in Apache Struts, we have also observed what we consider the same individual exploiting an Oracle WebLogic server vulnerability (CVE-2017- 10271), and also exploiting CVE- 2017-3066, a critical vulnerability of Java deserialization in the Adobe ColdFusion platform, "says Liebenberg.
If Rocke manages to exploit a known vulnerability to gain remote access to a server, Talos often tells the attacker to execute a shell script called A7 "that kills a variety of processes related to other cryptographic malware. – including those with names corresponding to popular mining malware like "cranberry", "yam" or "kworker" – in addition to me in general, like "minerd" and "cryptonight", "says Liebenberg. "It detects and uninstalls various Chinese AVs" and also downloads a file that uses a script that tries to connect to multiple IP addresses, via the Secure Socket Shell, and then download A7 on those systems and run it.
New Ransomware Continues to appear
Despite the increase in encryption attacks, ransomware is still a tool in the illegal arsenal of many cybercriminals.
The malware researcher Michael Gillespie, aka @ demonslay335 working with MHT, also runs the free ID Ransomware site, which allows ransomware victims to upload an encrypted file to ascertain the ransomware log that has encrypted your system.
ID Ransomware has 631 different ransomware strains – from Blue Blackmail, CryptGh0st and Dharma to ExecutionerPlus, Ryuk and Thanatos – up from 603 just two months ago.
Gillespie claims that his list is not exhaustive. For example, it does not count every new piece of ransomware based on Hidden Tear – open source code released by a researcher who claimed to want to see how ransomware worked – unless it includes important new features.
Hacker hacker: Why choose?
In some cases, however, hackers have opted to get illicit gains in more than one way.
"Obama's ransomware champion seems to have a miner's moner coins code in it – so after all you were already paying" Christiaan Beek chief scientist at McAfee security firm, tells the Information Security Media Group.
This type of strategy, however, is not new. "We saw components of cryptocurrency included in the ransomware kit that was released to compromised servers," the incident response expert David Stubley, who heads the Edinburgh security testing firm and 7 Elements advisor, tells the ; ISMG (see Hackers exploit the weak credentials of the remote desktop protocol ).
"In one of our recent engagements, we have seen the distribution of multiple ransomware kits, with varying levels of complexity and capacity," he says. "So, for example, one uses a" build your own "ransomware kit that [allows you to] decides on the amount of BTC [bitcoins] and the extension for encrypted files. While a more complex kit with mimikatz [a Windows password extraction tool] and crypto have been found also minimal capacities. "
Stubley states that the presence of different sets of exploit or crimeware tools and kits on the same endpoint could indicate that different attack groups had access to the same system. In many cases, he says, an early group of advanced attackers can get remote access to a system and spend weeks stealing interesting data. When they're done, they can install ransomware as a coup de grâce, or sell access to compromised systems to other less sophisticated attackers, who install cryptographic or ransomware software on endpoints.
"While knowing what the individual motivation is always difficult, it would seem that the most sophisticated attackers are using the most appropriate components, so if the mining business returns profit, they will use it," says Stubley. "Otherwise, they will automatically set themselves in ransoms."
[ad_2]Source link