 [ad_1]
[ad_1]
Quick grip:
- The XRP army has been targeted once again by scammers
- As with previous XRP scams, they promise community incentives and support for XRP owners
- Scammers are attempting to trick XRP holders by using Ripple-like websites and emails
- Ripple has asked XRP holders to be on the lookout for such scammers
- Ripple has not endorsed any XRP giveaways
Scammers are once again targeting the XRP community through an elaborate scam that promises incentives and support for XRP owners. According to the Ripple team, the scammers use a domain and email that trick recipients into believing the giveaway is from the company.
Beware of the latest free scam: There is a fake email and a fraudulent website that offers “Community Incentive Programs” or “XRP Incentive Plans”. Neither Ripple, nor any executive of our company, has offered, or will ever offer, free giveaways of digital assets.
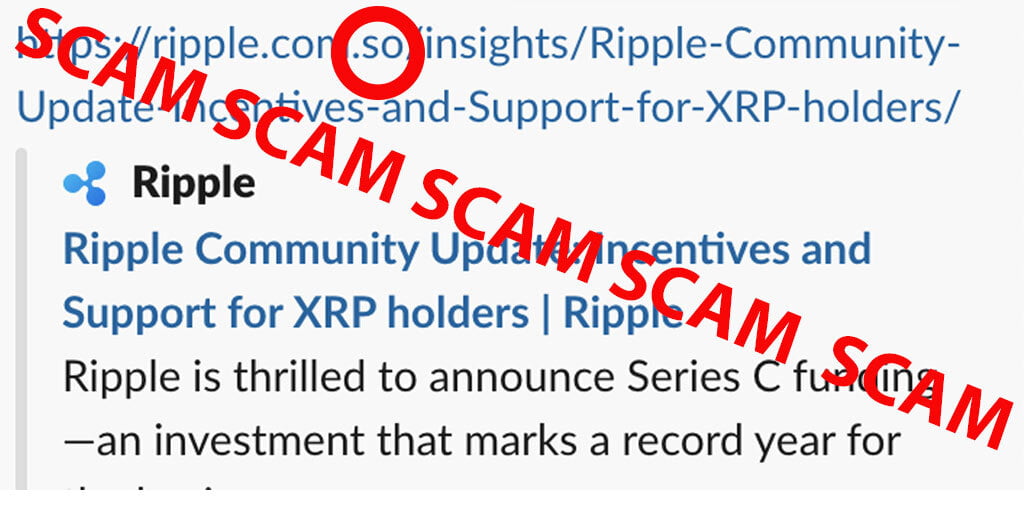
The team also provided the following screenshot which highlights the fake website with an additional “.so” which is not easy to detect.
 Ripple CEO: Hackers are using IDN homograph attacks
Ripple CEO: Hackers are using IDN homograph attacks
Ripple CEO Brad Garlinghouse also explained to investors that hackers were using “IDN homographic attacks” to deceive their victims. These types of attacks involve the use of similar domains like the one above ripple.com.so.
Additionally, hackers can play with the letters of the alphabet and numbers to create visual confusion. For example, RippIe.com with a capital “i” instead of the letter “l”.
Hello everyone except scammers who defraud people with fake XRP freebies. Hackers use IDN homographic attacks (e.g. capital I instead of lowercase l in ripple. Com, etc.) and these websites can stay active for months (despite reporting them) https://t.co/VdAp8BJc3W https: / /t.co / o3IRooNrzL
– Brad Garlinghouse (@bgarlinghouse) November 28, 2020
Ripple is not paying any giveaways
In conclusion, the Ripple team explained that the company is not paying any XRP giveaways. They also provided a link (below) for XRP investors to learn how to spot scams.
Any XRP giveaways are not approved, affiliated, maintained, authorized or sponsored by our company [Ripple]. For tips on how to locate #cracks, check out our blog here: on.ripple.com/3gADMQj
[ad_2]Source link