
[ad_1]
Most intelligent contracts have no verified source code, but people still trust them to protect their cryptocurrency. In addition, several large smart custody contracts have had security incidents. The security of existing contracts on the blockchain should be independently ascertainable.
Ethereum VM (EVM) Bytecode
The Ethereum contracts are compiled on EVM – the Ethereum virtual machine. As the blocks are extracted, EVM is executed and its resulting state is encoded forever in the blockchain. Everyone has access to this EVM code compiled for each intelligent blockchain contract, but directly reviewing EVM is not easy.
EVM is a stack-stack machine from the Harvard RISC architecture, which is quite distinct in the world of computer architectures. EVM has approximately 200 instructions that push and pop up values from a stack, occasionally performing specific actions on them (for example, ADD takes two stack arguments, adds them and pushes the result back into the stack). If you're familiar with reverse notation calculators (RPNs), stack machines will look similar. Stack machines are easy to implement but difficult to decode. Like reverse engineering, I do not have logs, local variables or arguments that I can label and track when I look at a stack machine.
For these reasons, I created Rattle, a framework that transforms the stack machine into an infinite -register SSA module.
Rattle
Rattle is a binary static EVM analysis framework designed to work on distributed smart contracts. Rattle accepts EVM byte strings, uses a flow-sensitive analysis to retrieve the original control flow graph, raises the control flow graph in an SSA / infinity form, and optimizes the SSA – by removing DUP, SWAP, PUSH and POP. Conversion of the stack machine into the SSA module removes 60% + of the EVM instructions and presents a much friendlier interface to those wishing to read the intelligent contracts they are interacting with.
Demo
As an example, we will analyze the infamous King of Ether contract.
First in Ethersplay, our Ninja binary plug-in to analyze Ethereum Smart Contracts:

Figure 1: The contract of the Ether king disassembled by Ethersplay
In Ethersplay, we can see there are 43 instructions and 5 blocks Basic. Most instructions are stack manipulation instructions (eg PUSH, DUP, SWAP, POP). Interlocated in the blocks are the interesting instructions (for example CALLVALUE, SLOAD, etc.).
Now, analyze the contract with Rattle and look at the output for the same function. We execute Rattle with optimizations, so the constants are bent and the unnecessary blocks are removed.
$ python3 rattle-cli.py - input input / kingofether / KingOfTheEtherThrone.bin -O
The Rattle CLI interface generates graphviz files for every function it can identify and extract.
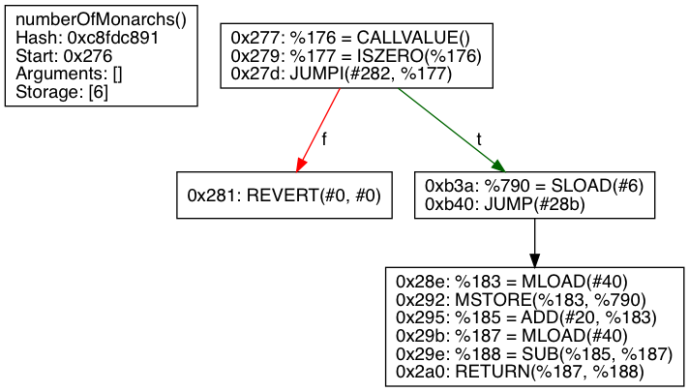
Figure 2: The King of Ether's contract retrieved by Rattle
As you can see, Rattle has optimized the numberOfMonarchs () function with only 12 instructions. Rattle has eliminated 72% of the instructions, the assigned registers that can be traced visually and removed an entire base block. In addition, Rattle has recovered the storage location used and the ABI of the function.
Rattle will help organizations and individuals to study the contracts they are interacting with and to establish an informed trust degree on contract security. If the source code of your contracts is not available or can not be verified, you must run Rattle.
Get Rattle on our GitHub and try it yourself.
*** This is a network of blog security bloggers syndicated by Trail of Bits Blog written by Ryan Stortz. Read the original post on: https://blog.trailofbits.com/2018/09/06/rattle-an-ethereum-evm-binary-analysis-framework/
Source link