 [ad_1]
[ad_1]
Kaspersky Labs, the leading cybersecurity unit, warned hackers to "reprofile" the best-known botnets in the world it in mass in order to spread their cryptocurrency mining malware as much as possible.
A new security bulletin shows the significant decline in 2018 in the price of Bitcoins and investor interest is not actually correlated with the collapse of cryptojacking episodes.
The researchers also stated that legislative control banned by world governments does little to reduce cryptojacker, since malware hidden in mines is commonly found in countries where cryptocurrency like Bitcoin it is completely illegal.
September sees upypk cryptojacking
While the number of unique users attacked by miners has certainly fallen from market fever at the beginning of this year, September has seen an increase for the first time in months.
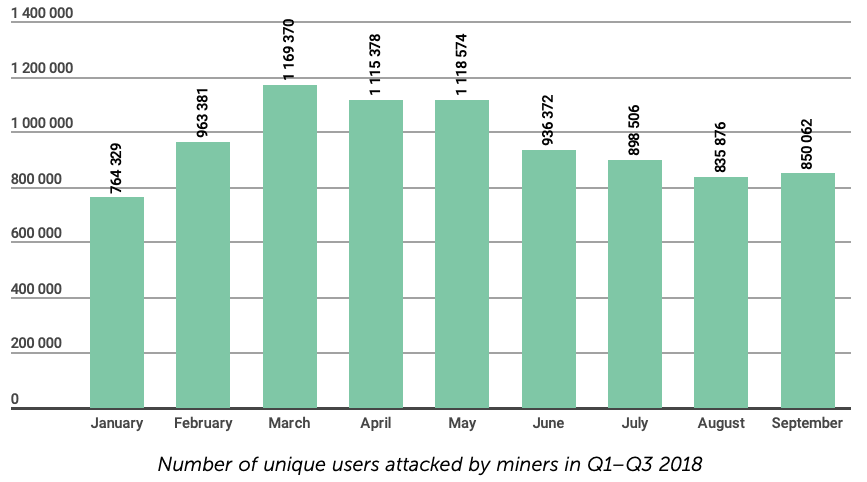
Kasperksy notes that botnet reprogramming has also led to a decline in DDoS attacks recorded in Q3 this year, since hackers believe that encryption is more lucrative and less competitive.
"This has been driven not only by the high popularity of cryptocurrencies, but also by the strong competition in the" DDoS market ", analysts wrote.[This] it made attacks less costly for customers, but not for botnet creators themselves, who still have to cope with more than a few non-legal "organizational problems". "
An example provided was the Yoyo botnet. The company has seen that Yoyo is now launching fewer DDoS attacks than before (despite the increase in activity at the start of this year), without the data suggesting to its owners (or the authorities) to have it dismantled.
Cryptojacking (and Monero) adapts to cybercriminals
Kaspersky elaborates the attractions of cryptojacking for cyber criminals: they usually manage to get away with it.
The researchers explain that it can be virtually impossible for the owner of an infected machine to realize that they are actively extracting the cryptocurrency. This greatly reduces the chances of attackers coming into contact with cyber-politics.
They also argue that Monero is still the most widespread cryptocurrency among illegally extracted coins, which can be generated by desktop browsers using standard common laptop processors.
"This is due to its anonymous algorithm, its relatively high market value and ease of sale, as it is accepted by most major cryptocurrency exchanges," Kaspersky reiterated. "For botnets that extract this money illegally, it is important that CPU resources can be used."
A few months ago, estimates suggested that the value of $ 250,000 of Monero was extracted each month through internet browsers, thanks to the alleged CoinHive cryptocurrency mining script.
Not long after, McAfee Labs revealed that hackers had released 2.5 million different versions of the screenplay in just three months.
You can not tie the cryptogens away
The analysts of Kaspersky have unfortunately concluded that the legislative control on cryptocurrencies "has a limited impact on the spread of the hidden [cryptocurrency] extraction."
In fact, the cryptographers are actually enjoying success in Algeria and Vietnam, where governments severely restrict or forbid access to cryptocurrency according to national law.
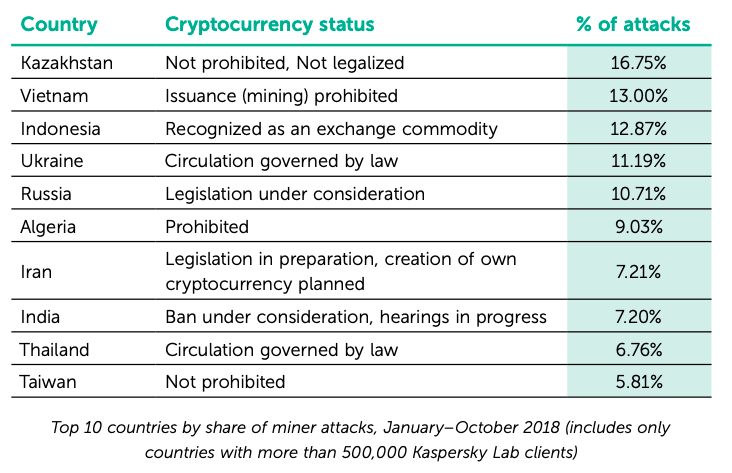
"Vietnam is [very high] in the rankings of […] countries by number of miners attacks and Algeria is sixth, "the researchers point out." Meanwhile, Iran, which is currently drafting legislation to govern cryptocurrency and is developing plans to issue its 39; coins & # 39 ;, is in seventh place. "
On the flip side, US Internet users are the least affected by cryptojacking so far in 2018, suffering only 1.33% of the total number of attacks, followed by the Swiss (1.56 percent) and the British (1.66 percent).
The company has found a realistic trend in the trend: the more freely unlicensed software is distributed in a country, the more harmful cryptocurrent miners are found.
Reportedly, this aligns with other Kaspersky statistics, which showed that miners of malicious cryptocurrency were commonly found in machines through pirated and unlicensed software.
Published November 28th 2018 at 15:56 UTC
[ad_2]Source link