 [ad_1]
[ad_1]
Cybercriminals are not leaving any stone unturned in their quest to illegally acquire Bitcoin. From hacking platforms to ransomware and cryptographic attacks, hackers adopt a multitude of sophisticated means to steal cryptocurrencies. Since 2017, the encrypted have become consistently more valuable. A handful of coins can get a strong price in fiat currency.
Despite the growing popularity of cryptocurrency worldwide, most of its technology has remained unchanged since it emerged in 2009. The sending of coins still requires the use of addresses almost impossible to remember. Therefore, many users have taken the habit of copying and pasting addresses when sending cryptocurrencies. Reports suggest that hackers have discovered a way to exploit this habit and steal Bitcoins in the process.
Malware details
Hackers know that many Bitcoin users choose to copy and paste Bitcoin addresses when they send and receive BTCs. So they created computer malware – a hijacker of cryptocurrency notes. Usually, this malware monitors between 400,000 and 600,000 addresses at a time. However, Bleeping Computer he recently discovered a clipboard hijacker that is monitoring more than 2.3 million Bitcoin addresses.
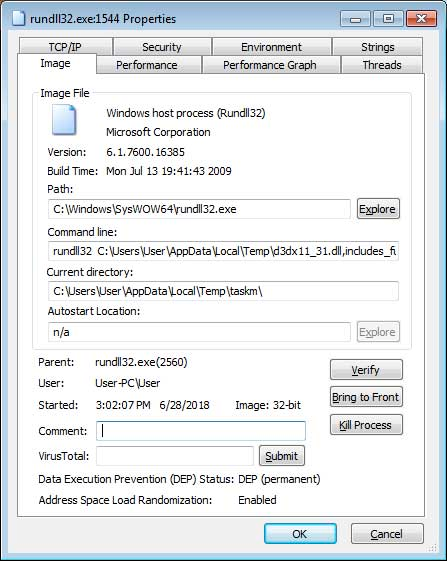
The address exchange virus was part of the All-Radio 4.27 Portable malware package. If a user has unknowingly installed this infected program, a malicious DLL would be added to the person's registry. This malicious DLL – d3dx11_31.dll creates an autorun program that works in the background, by running the exchange process.
How the clipboard hijacker malware works
This malware crawls into the Windows clipboard environment trying to detect Bitcoin addresses. Once the malware recognizes a BTC address, it is exchanged for another address owned by the hacker. It seems simple enough, but such an attack can have devastating consequences because there is no way to cancel a cryptocurrency operation once it is over.
The user may not know anything about the attack. Because hackers are not stealing funds directly from the wallet, none of the available security measures can counteract this exploit. The malware addresses an aspect of the cryptocurrency ecosystem that many claim is a security update over traditional network architecture.
In a sense, hard-to-remember addresses can be a bad thing, as well as a good thing. For example, if Bitcoin's address was an e-mail address, it would be more difficult to get such an attack successful.
How to protect your Bitcoin transactions from such attacks
The first step would be to have an updated antivirus program that can detect the presence of such a malware program. The cryptographic clip hijacker runs in the background, so its presence will probably not be obvious to the user.
The second step would be to always check the addresses before clicking the "send" button. When executing a transaction, open the notebook and paste the desired address into the program before pasting it into the wallet application. After doing so, copy any address and replace it in the open notepad. Eyepiece manually both addresses to see that they match. Repeat this step as many times as possible. It is useless to be in a hurry and end with a catastrophic blunder. You can complete the transaction when all checks have been completed.
What do you think of this latest threat of hacking cryptocurrency? Do you have any other useful safeguards against such an attack? Let us know in the comments section below
Image courtesy of Bleeping Computer.